Digest #03 - Linux namespaces and cgroups
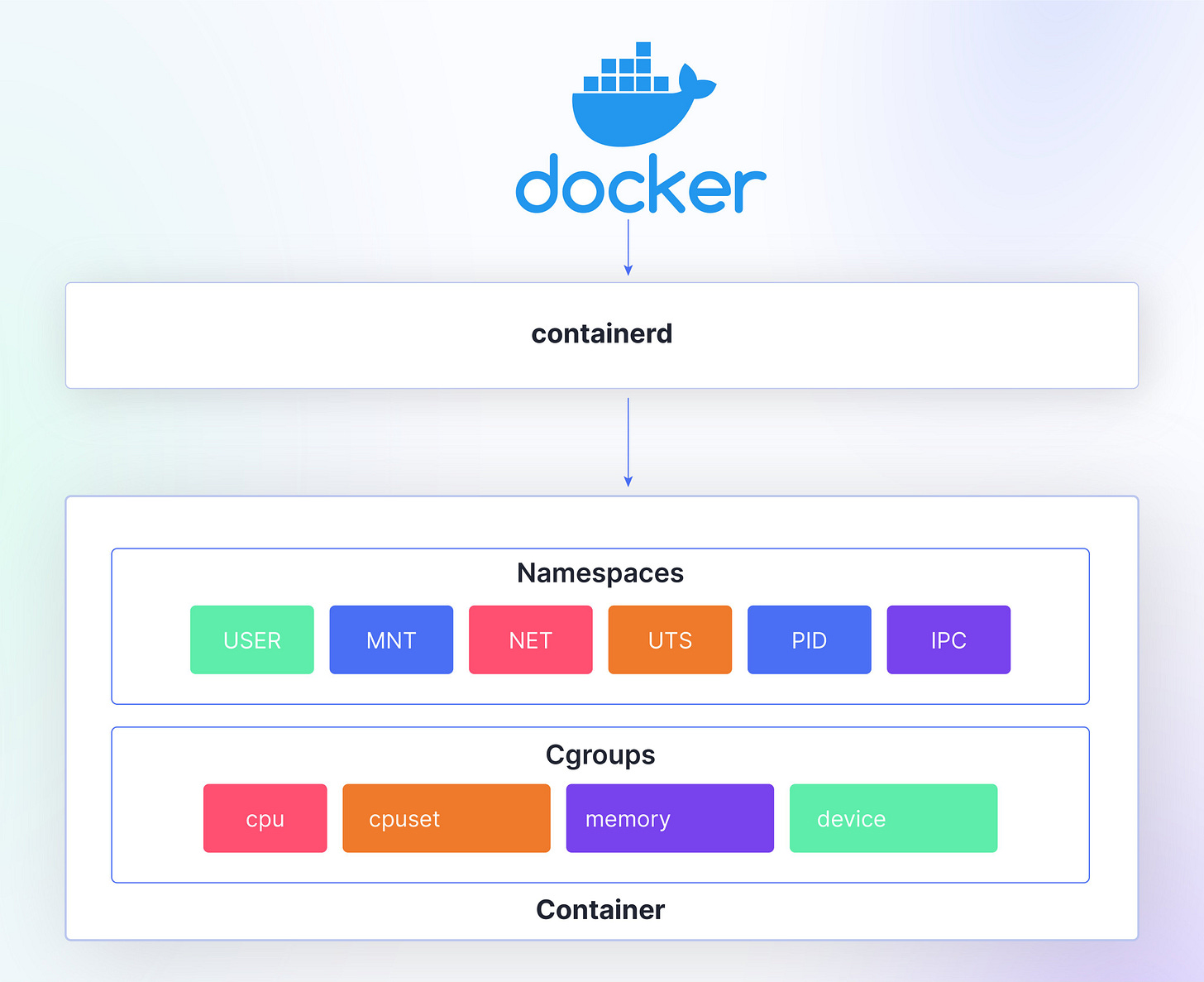
Linux namespaces are an important Linux kernel feature that separates system resources into isolated environments. Each namespace creates a separate instance of specific system resources, enabling processes within that namespace to have a unique view of those resources.
This isolation mechanism is crucial in modern container-based systems where multiple programs must coexist on the same server without interfering with one another.
In-depth look at each namespace
Now, let’s look at each namespace in greater depth.
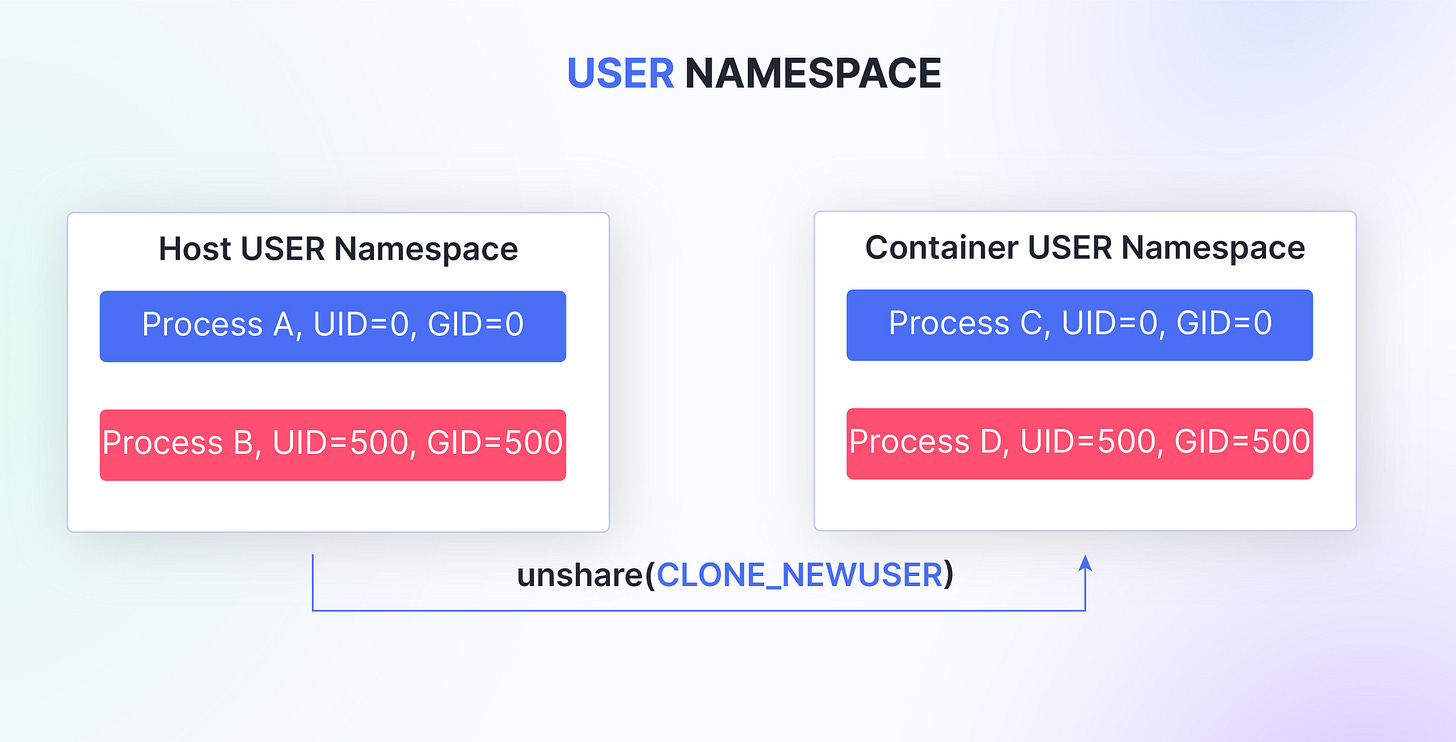
User Namespace
The user namespace isolates user and group IDs, ensuring that processes within a namespace have their own different set of user and group identities.
This allows for the creation of unprivileged user accounts within a container or namespace, without affecting the host system's user and group configurations. This is useful for implementing least-privileged execution environments and providing an additional layer of security.
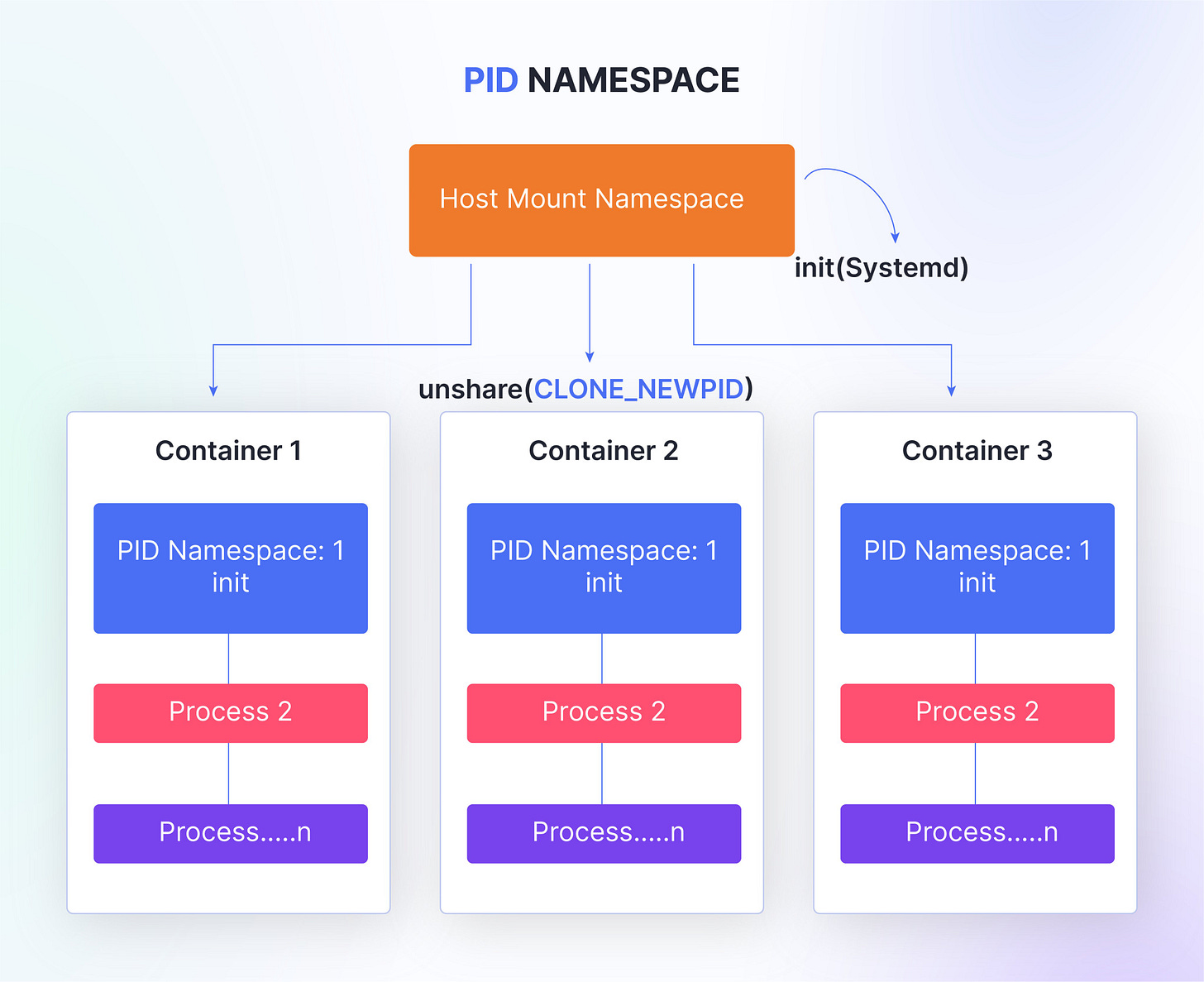
Process ID Namespace
The process ID (PID) namespace isolates the process ID number space, allowing each namespace to have its own set of processes with unique PIDs.
This namespace is important in containerization, as it prevents processes within a container from interacting with or viewing processes outside of their namespace.
Network Namespace
The network namespace provides isolation for network resources, including network interfaces, routing tables, and firewall rules.
Each network namespace has its own independent network stack, enabling the creation of virtual network environments with separate IP addresses, ports, and network configurations.
This namespace is important for applications that require network isolation or custom network configurations.
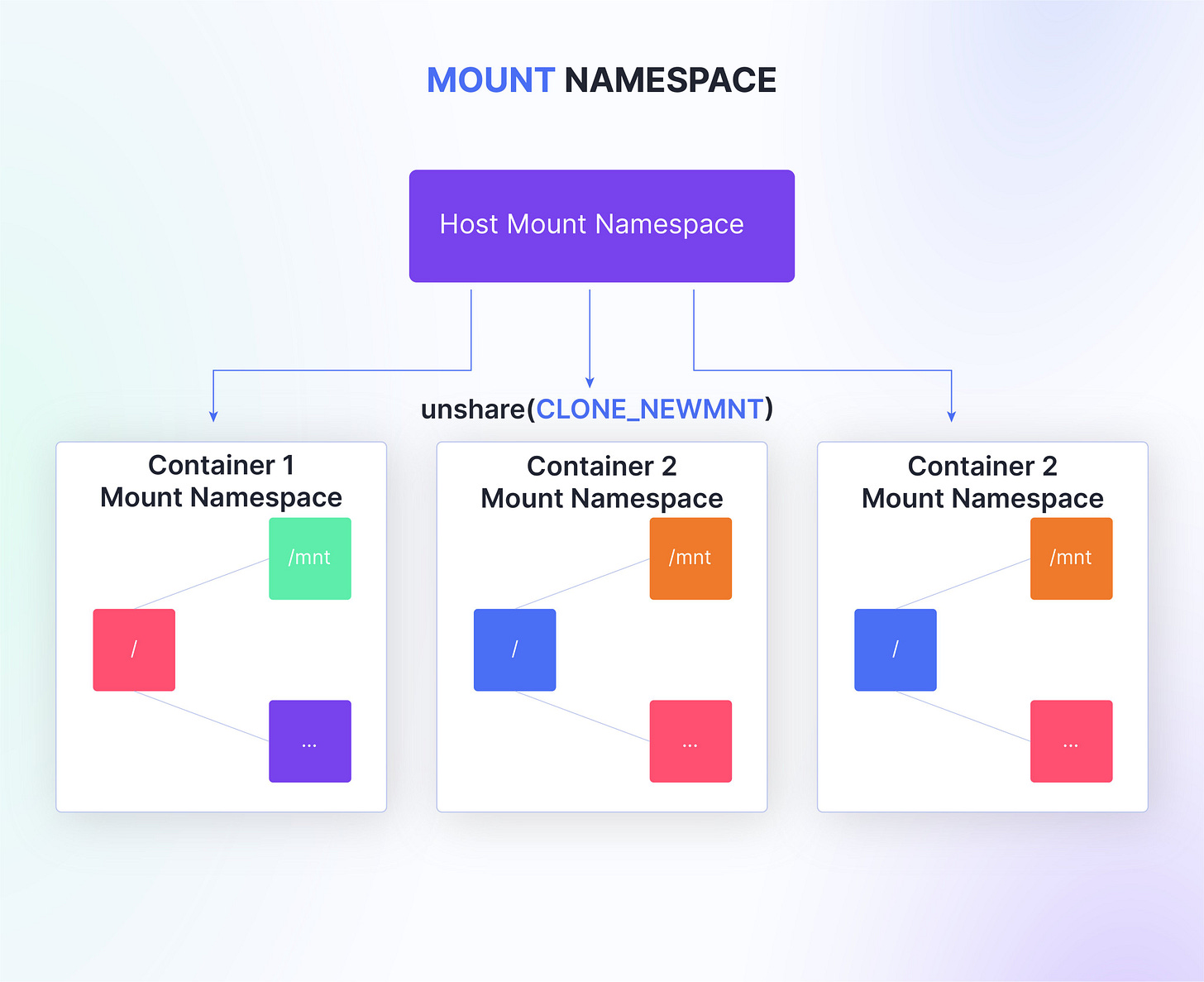
Mount Namespace
The mount namespace isolates the file system mount points, this means processes within a namespace will have a distinct view of the file system hierarchy.
It enables containers to have their own private file system mounts without affecting the host system's mounts. It also facilitates the creation of read-only or read-write file system layers, which is a common practice in container technologies
Interprocess Communication Namespace
The interprocess communication (IPC) namespace isolates various IPC mechanisms, such as System V IPC objects (shared memory, semaphores, and message queues) and POSIX message queues.
IPC namespaces ensure that IPC objects created within a namespace are visible only to processes within that namespace, preventing conflicts and providing isolation between different environments.
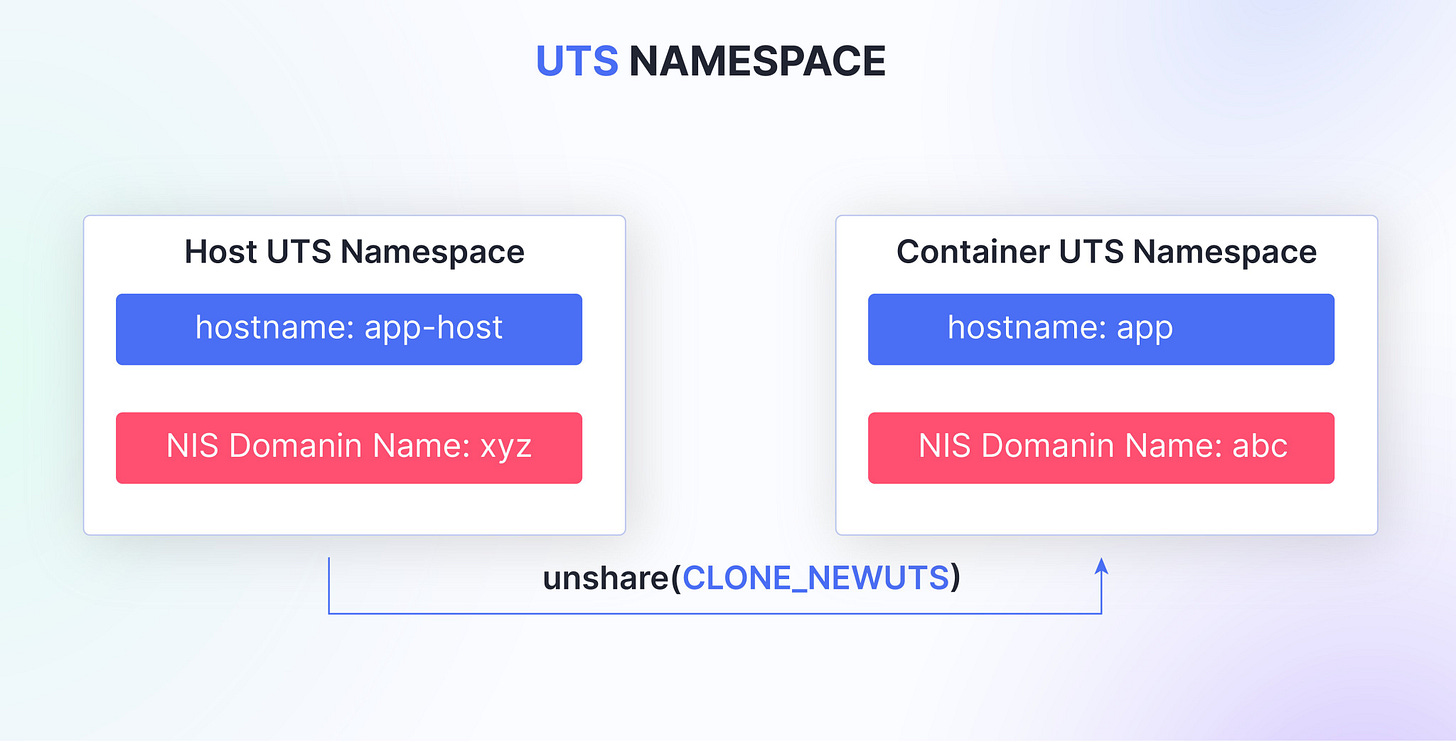
Unix Time-Sharing Namespace
The Unix Time-Sharing (UTS) namespace isolates the hostname and NIS/YP domain name, allowing processes within a namespace to have their own unique hostname and domain name.
How to List Namespaces in Linux
To list the namespaces associated with a process in Linux, you can use the lsns command.
This command provides information about the namespace types and their associated identifiers (IDs) for a particular process or process ID (PID).
$ lsns -p <process_id>
$ lsns
Control Groups (Cgroups)
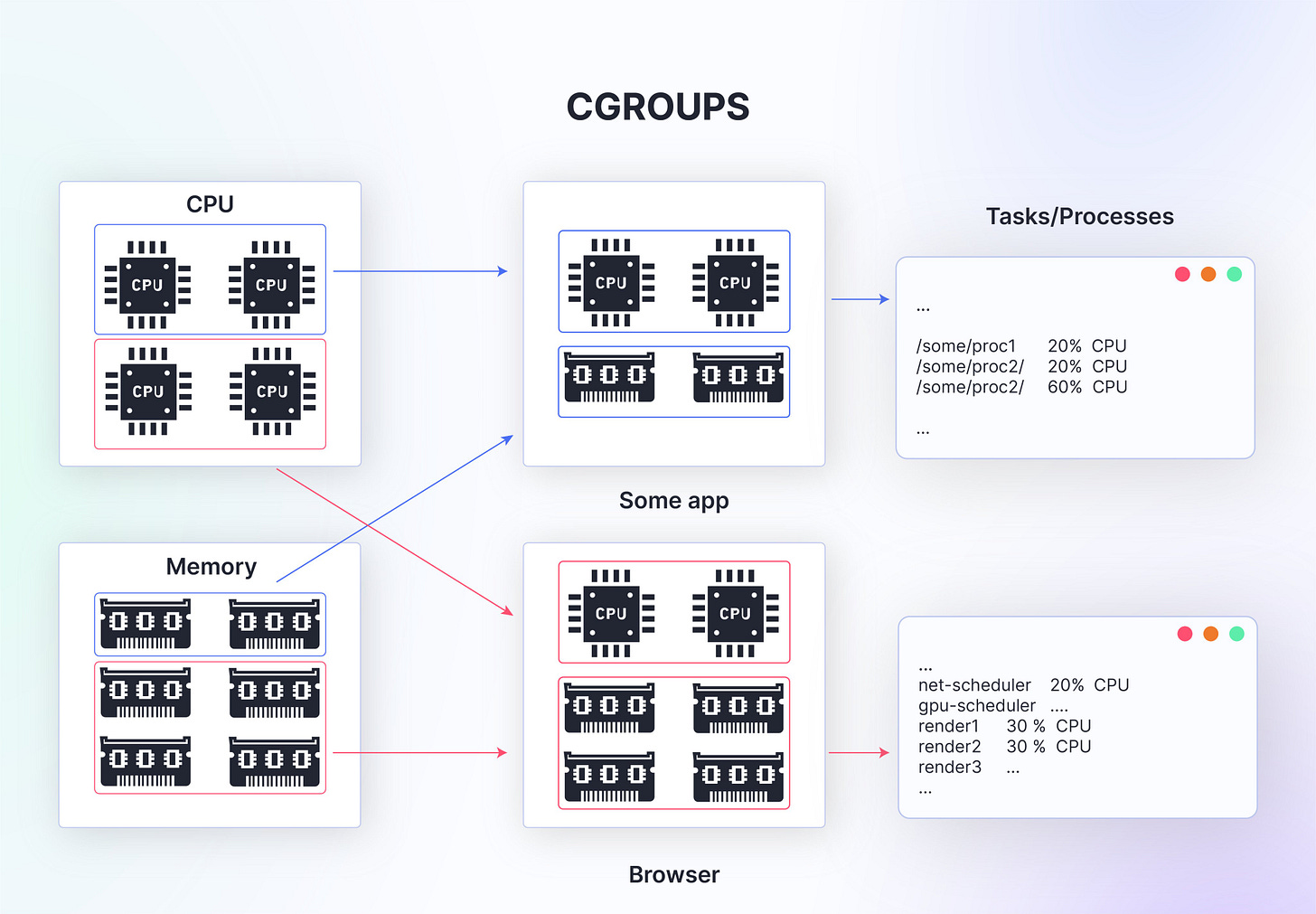
Cgroups, short for control groups, are a Linux kernel feature that complements namespaces by providing resource management and isolation capabilities.
While namespaces isolate system resources by creating separate instances, cgroups allow for the allocation and enforcement of resource limits, such as CPU, memory, disk I/O, and network bandwidth.
Cgroups organize processes hierarchically into control groups, enabling administrators to set resource limits and policies for each group.
These limits can be applied to individual processes or entire control groups, ensuring fair resource distribution and preventing resource exhaustion and noise neighbors.
Summing Up
That’s it for today. If you find this helpful, do a repost, it helps. Thank you.
If you have any questions, do let me know.