As a Linux superuser, understanding the /etc/shadow file is crucial for managing user accounts. This plain text file stores encrypted password information for system users. It has 640 permissions and is owned by the root user and shadow group.
A brief history
In early Unix and Linux systems, user account information, including encrypted passwords, was stored in the /etc/passwd file. This file was readable by all users, which posed a significant security risk. Malicious users could potentially access the encrypted passwords and attempt to crack them offline. As security concerns grew, the need for a more secure method of storing password information became apparent. This led to the development of the /etc/shadow file in the 1980s. The shadow password system was first implemented in SunOS and later adopted by various Unix-like operating systems, including Linux.
The introduction of /etc/shadow allowed for the separation of sensitive password data from other user account information, significantly enhancing system security. This change marked a crucial evolution in Unix and Linux security practices, addressing a longstanding vulnerability in user authentication systems.
Accessing the /etc/shadow File
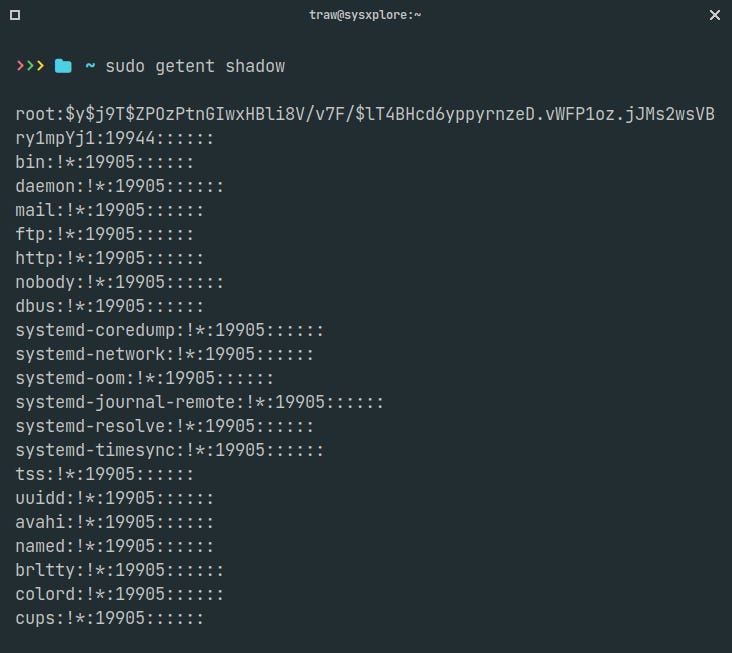
Due to its sensitive nature, the /etc/shadow file is only readable by the root user. To view its contents, you must have root privileges. You can use standard Linux file viewers such as cat, more, or less. Alternatively, use the following command:
$ sudo getent shadowFile Format and Structure
Each line in the /etc/shadow file represents a different user account. The root user is typically described on the first line, followed by system accounts and normal user accounts. New entries are appended to the end of the file.
Each record in the /etc/shadow file contains nine fields separated by colons:
username:encrypted_password:last_change:min_age:max_age:warning:inactive:expire:reservedLet’s view the root user's entry in the /etc/shadow file as an example:
$ sudo getent shadow | grep rootField Descriptions
Username: The unique login name used during the login process.
Encrypted Password: The password in
$type$salt$hashedformat. The$typerepresents the cryptographic hash algorithm:$1$: MD5$2a$: Blowfish$2y$: Eksblowfish$5$: SHA-256$6$: SHA-512
If this field contains an asterisk (
*) or exclamation mark (!), the user cannot log in using password authentication.Here is an example to list users who cannot log in using password authentication:
$ sudo getent shadow | grep '!*'Last Password Change: The number of days since January 1, 1970, when the password was last changed.
Minimum Password Age: The minimum number of days before the password can be changed (usually set to 0).
Maximum Password Age: The number of days before the password must be changed (default is 99999).
Warning Period: The number of days before password expiration that the user is warned to change their password.
Inactivity Period: The number of days after password expiration before the account is disabled.
Expiration Date: The date (in days since January 1, 1970) when the user account will be disabled.
Reserved: This field is currently unused and reserved for future use.
Summing up
That's all for this guide! Thank you for getting this far. I hope this guide has provided you with a better understanding of how user passwords are managed in Linux and the significance of each field in the /etc/shadow file.